Until recently, cybersecurity was widely viewed as a technical discipline; essential, but largely invisible to the wider organisation. That perspective shattered in 2025, when cyber-attacks on two of the UK’s most recognisable companies, Marks & Spencer (M&S) and Jaguar Land Rover (JLR), triggered enormous financial losses, supply-chain disruption and even contributed to a slowdown in national GDP growth.
These incidents demonstrated that cybersecurity is no longer confined to the IT department. It has become a business-critical, board-level, and even national economic issue.
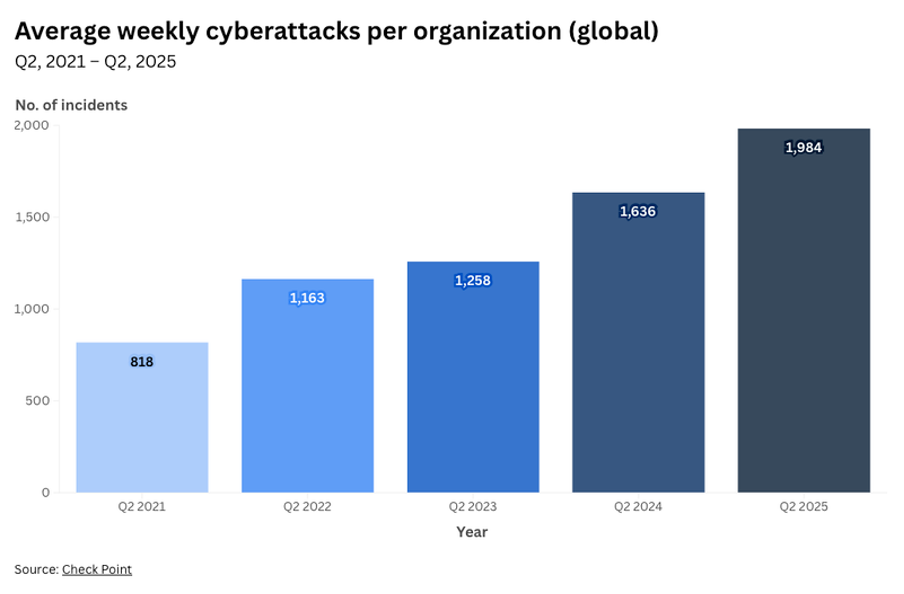
As the diagram from the World Economic Forum, sourcing from Check Point, demonstrates, each year the average weekly cyberattacks per organisation increases, demonstrating that each organisation is at higher risk from attackers.
As 2026 approaches, several major trends are reshaping how organisations must think about digital risk. Some trends reflect the growing sophistication of attackers; others highlight the need for stronger employee awareness, new regulatory conditions and more resilient supply chains.
But the message is clear: cyber-resilience is now foundational to business health and economic stability.
The M&S and JLR Attacks – A Wake-Up Call for the UK
In 2025, the UK experienced two of its most disruptive cyberattacks in modern history.
Marks & Spencer (M&S)
M&S was hit by a sophisticated attack that forced it to suspend online orders for weeks, disrupting logistics, distribution and customer services. The company projected a £300 million hit to operating profit (CNBC), with broader retail-sector impacts amounting to millions more. The breach originated via compromised third-party access; highlighting the scale of risk associated with external suppliers.
Jaguar Land Rover (JLR)
Several months later, JLR was struck by a devastating attack that shut down vehicle production at all UK factories. This single incident destabilised around 5,000 suppliers, severely affected the automotive supply chain and contributed to a measurable slowdown in UK GDP growth for the third quarter (0.3% to 0.1%) (The Guardian).
These attacks were not just “IT issues”. They were economic events, affecting manufacturing output, investor confidence, regional employment and national productivity.
Eight Key Cybersecurity Trends for 2026
1. The Rise of Ransomware-as-a-Service (RaaS)
Cybercrime has become industrialised. Under the Ransomware-as-a-Service model, criminal groups build powerful ransomware tools and lease them to affiliates.
RaaS is a subscription or affiliate-based model where criminal groups create sophisticated ransomware tools, then rent them out to other attackers. It’s essentially a criminal franchise model:
• The “provider” supplies ransomware kits, payment portals and tools.
• “Affiliates” (who may have limited technical skill) deploy the ransomware.
• Profits are shared between them.
This model means:
• More attackers (because skill barriers drop).
• More frequent attacks (because tools are packaged and ready).
• More sophisticated malware (because RaaS operators reinvest profits).
Combine RaaS with offensive AI tools, and you get scalable, automated attacks capable of adapting to environments, generating personalised phishing messages, or even using deepfake audio and video to impersonate employees (Expert Insights).
In 2026, experts expect RaaS to be a defining threat; integrated with AI to create faster, more targeted and more damaging attacks.
This lowers the skill barrier dramatically, meaning anyone, not just expert hackers, can launch sophisticated attacks. Expect more frequent, more damaging and more coordinated ransomware campaigns in 2026.
2. AI-Driven Attacks and AI-Powered Defences
AI is transforming the cybersecurity landscape. Attackers are now using AI to automate reconnaissance, craft personalised phishing emails, generate deepfake audio/video, and adapt malware in real time. In response, organisations will increasingly adopt AI-powered monitoring, behavioural analytics and automated incident response (Forbes). The cyber arms race is now running at machine speed.
The prompts the question of who will win out? It could go either way, with either side being better able to utilise AI to do the legwork to better drive efficiency.
3. Employee Behaviour as the Critical Weak Link
Despite all technological advances, most breaches still start with human error – careless clicks, weak passwords, misplaced trust or poor judgement under pressure. The M&S breach exposed how easily attackers can exploit people within a supply chain. In 2026, organisations must shift to continuous, realistic cyber-awareness training, make cyber-hygiene part of performance expectations, and enforce strict access controls.
How organisations can strengthen their human firewall:
• Move from annual training to continuous training: Short, frequent simulations and scenarios outperform one-off sessions.
• Train with realism: Phishing attempts should reflect actual company systems, internal communications, and emotional triggers.
• Audit all access – especially third-party suppliers: Contractors often have surprising levels of access, and attackers know it.
• Make cyber-hygiene part of performance culture: Employees take security seriously when it’s part of KPIs, in the way that customer satisfaction is part of many people’s KPIs, and job descriptions.
• Use “least privilege” and zero-trust policies: Don’t give employees, or suppliers, unnecessary access.
Humans will always be targeted, and employee behaviour have always been the weakest link in cybersecurity. But with the right strategy, they can become a powerful defensive asset.
4. Governments Taking a More Active Role in Cybersecurity
After witnessing the economic damage caused by JLR and other incidents, governments are stepping up. The UK is expanding regulatory oversight, mandating faster breach reporting, and investing in cyber skills and innovation. In 2026, national cybersecurity policy will become more assertive, treating cyber-resilience as a core element of economic and national security.
What’s changing in 2026:
• Stronger regulation through the UK’s Cyber Security and Resilience Bill, hopefully being implemented in 2026 or 2027. This expands oversight to more sectors, including supply-chain providers and managed services, and gives regulators greater proactive investigative powers (Gov.UK).
• Mandatory reporting of cyber incidents. Organisations will need to report breaches more quickly and more transparently.
• Increased public-private collaboration. Government will work directly with industry on threat intelligence, large-scale incident response, and national cyber exercises.
• More funding for cyber skills and innovation. Through the Cyber Growth Action Plan, the government is investing in skills pipelines, R&D, and cyber-startup acceleration.
• The UK’s National Cyber Security Centre (NCSC) will take a more proactive role; issuing stricter guidance, expanding threat-intelligence sharing, and increasing support for organisations responding to major cyber incidents (NCSC).
Cybersecurity has become public infrastructure; as critical as roads, energy and healthcare.
5. Supply-Chain Security Becomes Non-Negotiable
The JLR attack was a stark reminder that a company can be well defended, yet still vulnerable due to its ecosystem. When organisations are deeply interconnected, via logistics partners, software vendors, cloud platforms, or contractors, a single compromise anywhere in the chain can cause widespread disruption. In 2026, businesses must adopt ecosystem-wide security, not just self-focused security. That means supplier audits, contractual cyber requirements, shared incident protocols, and visibility tools that extend beyond internal networks.
6. Zero-Trust Architecture Gains Momentum
The traditional security perimeter is dead. With hybrid work, cloud platforms, and third-party integrations everywhere, identity now becomes the primary security boundary. In 2026, organisations will continue shifting to zero-trust models, where every access request is continuously verified, regardless of origin.
As more organisations adopt multi-cloud strategies and deploy edge devices, security complexity grows. Misconfigurations, inconsistent policies and limited visibility will create new vulnerabilities. 2026 will see increased demand for unified security platforms that provide centralised monitoring across diverse environments.
7. Manual Backup Processes and Clear Action Plans Become Essential
One of the biggest lessons from the 2025 attacks is that organisations crumble fastest when they lack manual backup procedures and clear, practised action plans. When core digital systems go down, logistics, payment processing, manufacturing, HR, supplier management, everything stops. In the JLR incident, production stalls were worsened because contingency processes could not immediately replace compromised digital tools.
In 2026, businesses will need to:
• Maintain offline, secure backups of critical systems
• Establish manual “break glass” procedures for core operations
• Conduct regular, realistic incident response rehearsals
• Train teams across the organisation, not just IT
• Build resilience so they can operate, even at reduced capacity, during a prolonged cyber incident
Cyber resilience is no longer about whether you can prevent an attack. It’s about whether you can survive one without catastrophic operational collapse.
8. Balancing Cybersecurity With a Seamless Customer Experience
Stronger cybersecurity often introduces friction: more authentication steps, stricter login rules, extra verification checks or blocked risky behaviours. For customers, every added hurdle risks lost sales, abandoned baskets or increased frustration. Retailers like M&S understand this tension acutely.
But in 2026, businesses will increasingly need to strike a smarter balance, strengthening protection without degrading user experience.
This will drive:
• Wider adoption of passwordless authentication (biometrics, passkeys)
• Smarter fraud detection that works silently in the background
• Risk-based authentication that only challenges users when behaviour appears unusual
• Simplified multi-factor authentication (MFA) flows
• UX design as a core consideration in security planning
The winners will be organisations that treat security not as a barrier, but as an enabler of trust, convenience and customer loyalty. Customers want to feel safe, but they also want a seamless journey. In 2026, the companies that get this balance right will stand out.
9. Cyber-Resilience Becomes a Core Business Strategy, Not a Technical Project
2026 will be the year companies finally recognise that cybersecurity is not just about preventing attacks, it’s about protecting operations, revenue, reputation and national infrastructure. Business continuity planning, crisis simulation, backup strategies, and executive-level involvement will become essential components of modern cyber-resilience.
Gone are the days when cybersecurity meant “preventing attacks.” The new reality is that breaches will occur; and the organisations that thrive will be those that:
• Design for resilience
• Build redundancies
• Maintain business continuity plans
• Understand their critical systems
• Test crisis responses regularly
In 2026, cybersecurity becomes synonymous with operational resilience, financial resilience, and brand resilience.
10. Quantum-Resistant Cryptography
Quantum computing poses a future threat to traditional encryption methods. While large-scale quantum computers are not yet mainstream, organisations are preparing for the post-quantum era. In 2026, expect:
• Adoption of NIST-approved post-quantum cryptographic algorithms.
• Increased investment in quantum-safe key management.
• Vendor pressure to demonstrate quantum resilience in security products.
Current encryption standards (RSA, ECC) could be broken by quantum algorithms like Shor’s. Early adoption of quantum-resistant cryptography will be a competitive differentiator.
11. Cybersecurity for IoT and OT Systems
The proliferation of connected devices—smart factories, autonomous vehicles, healthcare IoT—creates new attack surfaces. Many IoT and OT systems lack robust security controls, making them prime targets.
Key developments in 2026:
• Mandatory IoT security standards for manufacturers.
• Increased deployment of network segmentation and anomaly detection in OT environments.
• Growth of IoT-specific threat intelligence platforms.
A single compromised sensor or controller can disrupt entire production lines or critical infrastructure.
Conclusion: Cybersecurity Is Now an Economic Imperative
The M&S and JLR attacks were more than corporate crises; they were national disruptions with measurable economic impact. As attackers innovate and organisations become more interconnected, the stakes continue to rise.
The year ahead demands:
• Smarter technology
• Stronger regulations
• Better-trained employees
• Resilient supply chains
• Close public–private cooperation
• Board-level leadership.
Cybersecurity is no longer something companies “manage.” It’s something they depend on for survival, reputation and long-term stability.
Sources:
https://www.weforum.org/stories/2025/09/cybersecurity-awareness-month-cybercrime-ai-threats-2025/?utm_source=x&utm_medium=social
https://www.cnbc.com/2025/05/21/ms-cyberattack-to-wipe-out-nearly-one-third-of-annual-profits.html
https://www.theguardian.com/business/2025/nov/13/uk-economy-grew-by-just-01-in-third-quarter-amid-jlr-cyber-attack-hit
https://expertinsightsinc.com/cybersecurity-trends-2026
https://www.forbes.com/sites/bernardmarr/2025/09/26/the-7-biggest-cyber-security-trends-of-2026-that-everyone-must-be-ready-for
https://www.gov.uk/government/collections/cyber-security-and-resilience-bill
https://www.ncsc.gov.uk/files/ncsc-annual-review-2025.pdf
